December  2016
2016
Navigating HIPAA-Compliant File Sharing
By John Hurley
For The Record
Vol. 28 No. 12 P. 30
Once health care organizations enter the labyrinth of regulations known as HIPAA, it can be difficult for them to find their way out. At every turn, they are confronted with the consequences of noncompliance, including fines numbering in the millions, a year in jail, and, even worse, a complete loss of public trust.
When it comes to HIPAA-compliant file sharing, it's even harder to navigate the maze, especially as more providers go mobile.
How can health care firms and businesses overcome the difficult quest that is HIPAA-compliant file sharing? Perhaps the biggest key is to gain a comprehensive understanding of the HIPAA technical regulations that affect file sharing.
Does HIPAA Affect Me?
HIPAA regulations cover more than just hospitals and physicians; any business that deals with protected health information (PHI) in any way must follow the regulations.
Consider how the death of musician Prince was reported. Leaks and details of drug use and administered medications ushered in speculation on whether the music legend's HIPAA rights were violated. Where did these leaks originate? Allegedly from anonymous health care sources talking to celebrity gossip outlets. This has not been proven, but if it does turn out to be true, the providers could suffer serious consequences.
It's likely that if an organization distributes or receives PHI, it will have to follow HIPAA regulations. According to Health & Human Services (HHS), these covered entities (CEs) include the following:
• health plans, including health insurance companies, HMOs, and government programs such as Medicare and Medicaid;
• most health care providers, including those that conduct business electronically, such as clinics, physicians, hospitals, psychologists, chiropractors, nursing homes, dentists, and pharmacies; and
• health care clearinghouses, entities that process nonstandard health information received from or sent to another entity in a standard format.
However, HIPAA compliance doesn't stop with CEs. Third-party contractors, known as business associates (BAs), need access to patient records. These organizations include the following:
• billing and claims processing organizations;
• those that help administer health plans, including IT specialists, lawyers, and accountants; and
• vendors who manage the digital or physical storage and destruction of medical records.
While BAs are not held to the same standard as CEs, contracting with a regulated industry can be a necessary hassle. If a CE or BA shares files, it must meet benchmarks that constitute HIPAA-compliant file sharing.
How can organizations prepare?
The Three Security Standards
HIPAA's set of security standards fall into the following three categories: administrative, physical, and technical.
Running the gamut from employee training to encryption, these standards attempt to protect patient information from internal and external threats. Some standards are required, while others are merely recommended.
CEs that fail to implement the required standards may be liable for a breach, which can have serious consequences. Besides uncovering the most egregious HIPAA violations (see infographic), HHS conducts hundreds, if not thousands, of routine investigations each year.
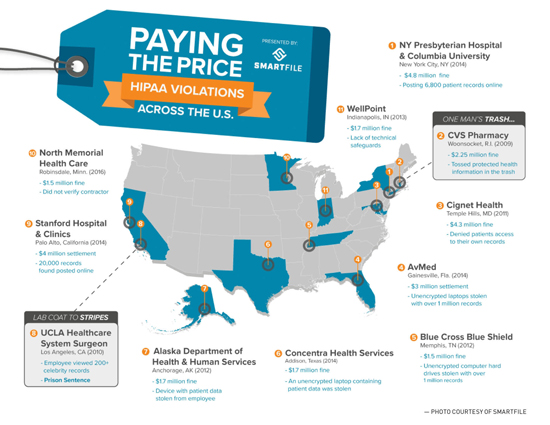
What steps can IT departments take to avoid becoming just another HIPAA violation on the map?
HIPAA 101
Within the three safeguard categories (administrative, physical, and technical) are myriad IT-related regulations. The technical safeguard, which the Security Rule defines as "the technology and the policy and procedures for its use that protect electronic [PHI] and control access to it," largely affect file sharing.
Within the technical safeguards, there are the following four criteria:
• access and audit control;
• transmission security;
• integrity; and
• person or entity authentication.
The Security Rule was intended to be "technology neutral," meaning it does not endorse or recommend any one technology, relying on organizations to perform due diligence in their search for a HIPAA-compliant solution. As a result, CEs must be discerning in choosing products that adhere to HIPAA-compliant file sharing standards.
Access and Audit Control
Access controls offer the following actionable items:
• User identification (required). Every user must be assigned a unique name or number to identify them and track their activity.
• Emergency access procedure (required). In the case of an emergency such as a power outage or a natural disaster, an established plan must be in place to access electronic PHI. While this does not necessarily affect BAs, CEs must have a backup or emergency failover solution.
• Audit controls (required). Audit controls can be in the form of hardware, software, and/or procedural methods. These controls monitor activity in devices or networks that contain or use electronic PHI. In terms of file sharing, these controls come into effect in cases such as user analytics.
• Automatic logoff (recommended). Not all protocols are required, but to play it safe, CEs should institute these preventative measures to ensure the safety of their networks and PHI. Automatic logoff allows a session to be terminated after a predetermined period of time. This safety feature makes it difficult for unauthorized employees to gain access to data. Additionally, this feature is built into most software, making it easy to implement.
• Encryption and decryption (recommended). While not a requirement, encryption and decryption can protect PHI and spare CEs from future issues.
Transmission Security
Transmission security aims to protect data as they are being transmitted through the network. Information that is cloned, altered, or deleted can result in noncohesive data and possibly endanger patients.
In the Security Rule, HHS recommends CEs examine internal procedures for flaws and implement a transmission security plan that best suits their needs. Begin by analyzing the current methodology for transmitting patient information, whether via e-mail, the internet, or in person. Considerations include the following:
• Integrity controls (recommended). Integrity control involves implementing security measures that protect data sent electronically. These controls help to ensure that the original data cannot be changed (especially maliciously) without detection. Integrity controls can take different forms, including using granular permissions to prevent outsiders from viewing data.
• Encryption (recommended). Although this is optional, encrypting data during transmission should be a high priority.
Integrity
Integrity, which also calls for transmission security, takes steps to protect data from being tampered with or changed without proper authorization. When transmission security fails, there must be a backup protocol to ensure the information remains accurate and unchanged.
A mechanism to authenticate electronic PHI is recommended. Possibilities include checksum verification or digital signatures. When transmission fails, HHS advises using a secondary authentication procedure.
Person or Entity Authentication
Authentication is required to verify that entities or individuals accessing electronic PHI are who they say they are. Examples of authentication include employee IDs and thumbprint scanners.
Finding Help
When searching for a HIPAA-compliant file-sharing solution, be sure the tool includes the following features:
• granular permissions;
• firewalls or backup;
• user auditing;
• password-protected sharing;
• user and password management tools; and
• encryption and decryption.
When it comes to implementing compliant technologies, HIPAA regulations are subjective. As a result, the term "HIPAA compliance" can mean different standards for each compliant organization.
In certain cases, CEs require a BA agreement (BAA) from file sharing or cloud platforms. There is no specific template for these agreements—the CE sets the specific requirements a file service must meet.
If the CE does not require a BAA, a HIPAA compliance statement is recommended. This can be a checklist of the features or actions a business is expected to maintain while the solution is being used by the entity.
For CEs and BAs, HIPAA-compliant file sharing can make the process to compliance seem neverending. However, with the right policies and technology, organizations can ensure their reputation remains intact as they safeguard the PHI of patients, providers, and fellow health care organizations.
— John Hurley is CEO of SmartFile.



